Cybersecurity break-ins are a worldwide problem. With over 40 billion hacks each year through the World Wide Web, the numbers are mind-boggling. The costs are similarly high: governments and businesses can expect to lose roughly $400 billion annually in damages and property loss due to such attacks. As the number of devices grows with an ever-more-connected Internet of Things (IoT), the potential for damage is escalating. Yet the best tools of the era – firewalls, encryption keys, and “honeypots” (dummy servers to trap hackers) – frequently fail.
Kenneth Wong, recent Bachelor of Technology Forensics Investigation grad, in BCIT’s Digital Forensics and Cybersecurity Option, recently presented his graduating project at two international conferences.
Applied Digital Forensics and Cybersecurity
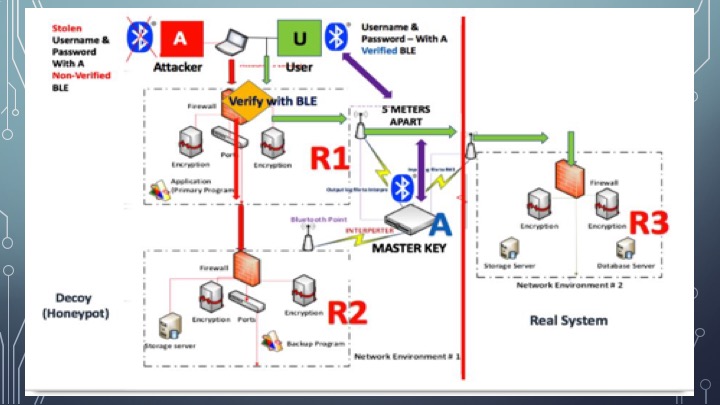
Kenneth’s approach tracks the behaviour of an attacker, and then limits their ability to compromise a cybersecurity system. Along with cybersecurity instructor Dr. Aaron Hunter, Kenneth developed a system that combines a decoy with a real system and has a Bluetooth Low Energy (BLE) controller inserted in between.
“Using the BLE to lock and unlock servers, much like using multiple access doors, the system transfers data securely and safely, without allowing potential attackers to notice any transfer being processed throughout the system,” explains Kenneth.
Kenneth built the system using Raspberry PI and Arduino boards to replicate servers that communicate wirelessly, and wrote custom programs to monitor attacker behaviour. His relatively low-cost solution aims to lower disruption to the live system, capture the attacker’s position, and limit the potential for damage. The system also seeks to hide from the attacker so they don’t know they’re being monitored, and to gather potential evidence against attackers for further investigation.
International stage
Conference reviewers praised the approach for its potential, given the frequency of IoT attacks, and the successful practical demonstrations of the solution in a network environment similar to those used in real companies.
Kenneth enjoyed the opportunity to present the work with Aaron at the Institute of Electrical and Electronic Engineers (IEEE) Conference on Communications and Network Security (CNS), in Las Vegas and at the International Conference on Information Systems Security and Privacy – Institute for Systems and Technologies of Information (ICISSP) in Portugal.
“Forensic instructors Dr. Joe Ilsever and Patrick Neil also mentored me and gave me valuable advice,” adds Kenneth, “the program was an incredible journey.”

Fantastic!
Great Work Ken!